General Discussion
Forum home - Go back to General discussion
|
Be extra careful about email attachments. CryptoLocker Virus can wipe you out!
|
|
|
« Back ·
1 ·
Next »
|
|
|
Return to top of page · Post #: 1 · Written at 9:01:20 PM on 29 September 2015.
|
|
|
|
Location: Sydney, NSW
Member since 28 January 2011 Member #: 823 Postcount: 6933 |
|
Some may feel that it goes without saying that you should be extremely careful about opening email attachments from unknown senders, but I feel that it cannot be said often enough. |
|
|
Return to top of page · Post #: 2 · Written at 7:03:14 PM on 30 September 2015.
|
|
|
|
Location: Bathurst, NSW
Member since 7 August 2008 Member #: 336 Postcount: 412 |
|
Ransomeware is running around, have seen comments on other forums. |
|
|
Return to top of page · Post #: 3 · Written at 7:19:17 PM on 30 September 2015.
|
|
|
|
Administrator
Location: Naremburn, NSW
Member since 15 November 2005 Member #: 1 Postcount: 7607 |
|
As a general rule I don't open anything that I didn't send for. It is automatically deleted without being opened if it even smells like being a malicious message. ‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾ A valve a day keeps the transistor away... |
|
|
Return to top of page · Post #: 4 · Written at 12:23:08 AM on 1 October 2015.
|
|
|
|
Location: Sydney, NSW
Member since 28 January 2011 Member #: 823 Postcount: 6933 |
|
Apparently the encryption is so tough no one knows how to recover the affected files. |
|
|
Return to top of page · Post #: 5 · Written at 2:22:06 AM on 1 October 2015.
|
|
|
|
Location: Oradell, US
Member since 2 April 2010 Member #: 643 Postcount: 835 |
|
It's a good move to not trust attachments in emails, even from known people (I've had my email account hacked by spammers). In my address list, I have my own email listed along with friends'. So if I see spam from my own email account, then I know it's time to change my password. |
|
|
Return to top of page · Post #: 6 · Written at 12:45:50 PM on 1 October 2015.
|
|
|
|
Location: Sydney, NSW
Member since 28 January 2011 Member #: 823 Postcount: 6933 |
|
occasionally I get emails from banks where I don't have accounts... |
|
|
Return to top of page · Post #: 7 · Written at 6:59:00 PM on 1 October 2015.
|
|
|
|
Location: Wangaratta, VIC
Member since 21 February 2009 Member #: 438 Postcount: 5679 |
|
Of course this is like RFI Generating & Dodgy electrical stuff. All we seem to have is a reporting service & statutory authorities that sit back, take no ownership & do naught about it. |
|
|
Return to top of page · Post #: 8 · Written at 7:57:00 AM on 3 October 2015.
|
|
|
|
Location: Hill Top, NSW
Member since 18 September 2015 Member #: 1801 Postcount: 2241 |
|
I've seen a PC that was infected by the AFP virus. The only solution was to wipe it and start over. |
|
|
Return to top of page · Post #: 9 · Written at 8:42:36 AM on 3 October 2015.
|
|
|
|
Administrator
Location: Naremburn, NSW
Member since 15 November 2005 Member #: 1 Postcount: 7607 |
|
This e-mail is believed to send people's computers to a similar fate. Screenshot below from my mobile phone. 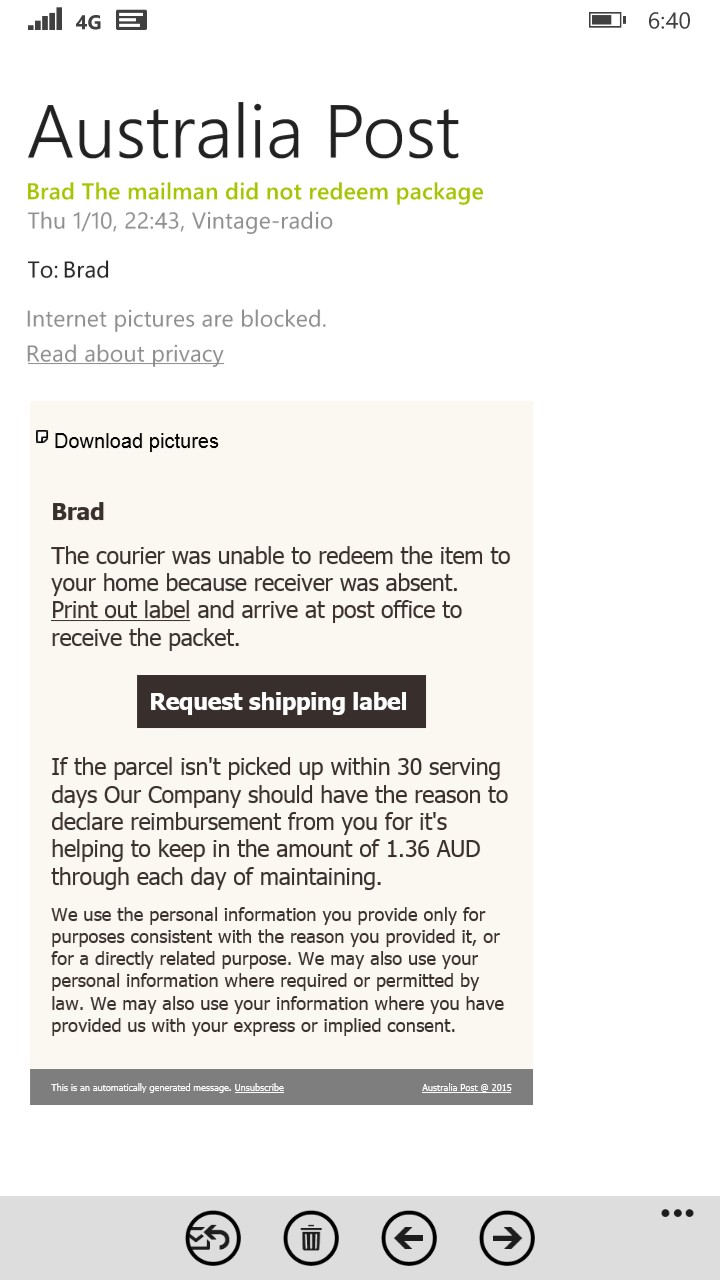 The language and terms used in the sentences is usually a giveaway. Australia Post doesn't normally use terms such as "shipping" or "mailman" in their correspondence and they do not charge recipients for items that are not delivered. If you get this one, just bin it. ‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾‾ A valve a day keeps the transistor away... |
|
|
Return to top of page · Post #: 10 · Written at 6:32:33 PM on 3 October 2015.
|
|
|
|
Location: Sydney, NSW
Member since 28 January 2011 Member #: 823 Postcount: 6933 |
|
Yep, that's the type of message I alluded to, carrying a cryptovirus payload as an attachment. |
|
|
« Back ·
1 ·
Next »
|
|
|
You need to be a member to post comments on this forum.
|
|

Sign In

Vintage Radio and Television is proudly brought to you by an era where things were built with pride and made to last.
DISCLAIMER: Valve radios and televisions contain voltages that can deliver lethal shocks. You should not attempt to work on a valve radio or other electrical appliances unless you know exactly what you are doing and have gained some experience with electronics and working around high voltages. The owner, administrators and staff of Vintage Radio & Television will accept no liability for any damage, injury or loss of life that comes as a result of your use or mis-use of information on this website. Please read our Safety Warning before using this website.
WARNING: Under no circumstances should you ever apply power to a vintage radio, television or other electrical appliance you have acquired without first having it checked and serviced by an experienced person. Also, at no time should any appliance be connected to an electricity supply if the power cord is damaged. If in doubt, do not apply power.
Shintara - Keepin' It Real · VileSilencer - Maintain The Rage
